Software vulnerabilities are among the most commonly exploited breaches by cybercriminals, from the SolarWinds attack impacting over 18,000 organizations to the Log4j vulnerability affecting over 48.3 percent of organizations globally. Vendors’ security risk management abilities are being challenged now more than ever before.
When it comes to security risk management, incident response is usually the first thing that comes to mind. While it is crucial to have an incident response plan in place to address the aftermath of a breach, it is equally important to prioritize software security at the development stage to prevent such incidents from occurring in the first place.
Guided by NIST Secure Software Development Framework (SSDF), Security Development Lifecycle (SDL) is an increasingly common practice that provides a systematic approach that minimizes security risk and ensures compliance with regulatory requirements. Different companies may have their own definition of SDL, yet the fundamental remains the same, helping developers standardize and build a highly secure product from start to finish.

How does Synology do it?
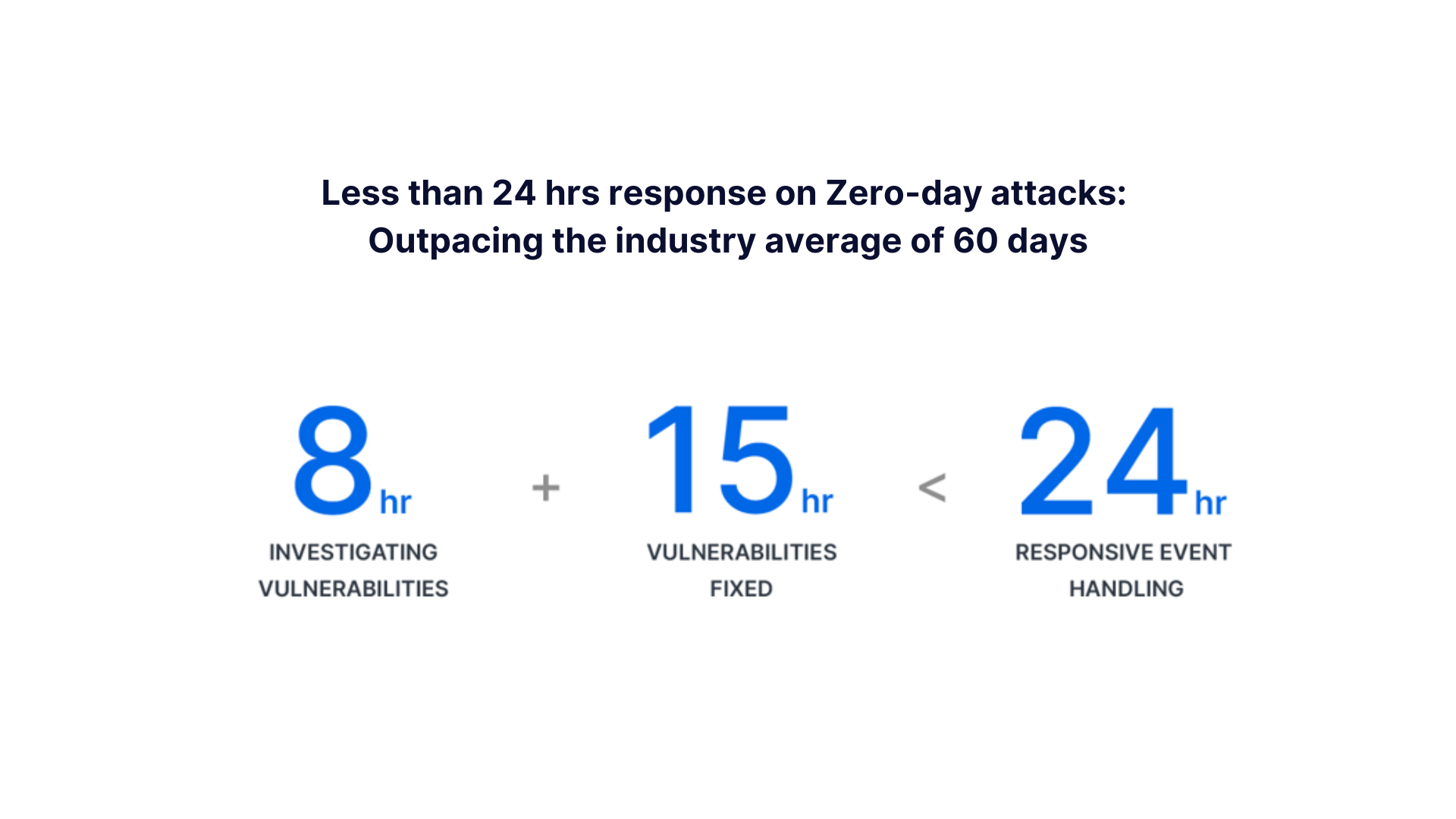
As a storage vendor our clients entrust their valuable data with, Synology makes security our top priority. Our dedicated Product Security Incident Response Team (PSIRT) designed a four-phase software development process (Design, Development, Verification, Release) to ensure product safety and quick response to zero-day attacks. We promise to fix critical vulnerabilities within 24 hours, outpacing the industry average of 60 days. Our commitment to security is evident as there are no existing exploits on Synology products according to the KEV Catalog by Cybersecurity & Infrastructure Security Agency (CISA) since introduced in 2021.
This article will explore how Synology products are carefully cultivated following our own SDL, in pursuit of security.
1. Design phase: Secure by design
When a new Synology product or feature is put in place, the Product Security Assurance (PSA) Program will be initiated. The PSIRT team then collaborates with the development team in reviewing the security infrastructure and design, offering constructive suggestions for improvement. For instance, the root privilege was removed in DSM 7.0 to adhere to the least privilege principle, granting users only the minimum necessary permissions to reduce security risks. This proactive approach establishes a strong security framework from the outset, avoiding future security-related complications.
2. Development phase: Standardized and automated testing
The development phase will officially commence after the product specifications have been confirmed. To ensure the quality of the code from the start, Synology implements Static Application Security Testing (SAST) with automatic tools to screen out potential vulnerabilities and defects. This helps prevent the use of insecure or forbidden source code from the get go.
As the development progresses and reaches completion, Dynamic Analysis Security Testing (DAST) will be performed on an ongoing basis to detect changes in the code and ensure that all functionality is thoroughly tested on the application, reducing potential security threats.
3. Verification phase: The attackers’ mindset
At Synology we understand the importance of thorough testing and verification before releasing our products to users. That’s why we introduced the Synology Red Team in early 2022. Comprised of a talented group of in-house hackers with extensive professional experience, the Red Team is dedicated to examining our products from an attacker’s perspective to identify and exploit any vulnerabilities. In just six months, the Red Team has already made a significant impact, identifying over 21% of system bugs, equivalent to US$100,000 in bounty program rewards, before the official release.
Speaking of bounty program, we don’t just rely on our in-house team to secure our products. We take a proactive approach and actively engage with the hacker community through various initiatives. Our participation in prestigious events like Pwn2Own and TienFu Cup and our annual bug bounty program since 2017, where we invite external researchers to help us identify security vulnerabilities, demonstrates our commitment to the safety of our users’ data. To date, over 200 researchers have participated in our bug bounty program, and we have rewarded more than US$270,000 for their efforts.
By embracing the attackers’ mindset, we are able to simulate real-world attacks and thereby improve our readiness in the event of an actual crisis. This proactive approach sets Synology apart from the competitors and ensures that our users can trust in the security and reliability of our products.
4. Release phase: Industry-leading response time
If the red team is playing offense, then the blue team is playing defense. The Red Team actively seeks out vulnerabilities while the Blue Team vigilantly monitors for security threats. Upon reporting of a vulnerability, the Blue Team promptly initiates a preliminary assessment to determine the impact within eight hours. Once identified as critical issue, the vulnerability will be promptly remediated within 24 hours, significantly outpacing the industry average of 60 days of mean time to remediate (MTTR).
Following the release of a patch, PSIRT will issue a Security Advisory to inform our users and publicly announce the software update simultaneously. User feedback is also reported back to the team. Our prompt and effective response ensures that our users can consistently trust in the security of our products, as security is always a top priority at Synology.
Tips to driving MTTR efficiency? Transparency is key.
One may wonder how Synology achieves such an exceptional Mean Time to Remediate (MTTR) when facing a zero-day attack. The key lies in keeping a transparent inventory.
When developing an application, numerous of open-source components are typically required. For instance, each version of Synology DSM includes over 1,600 open-source components. In the event of a zero-day vulnerability being discovered, having an inventory system in place can help quickly determine if Synology products are impacted, and more specifically, which applications and versions are affected.
Software Bill of Material (SBoM) is a comprehensive inventory system that tracks all third-party and open-source components used in a software application offering transparency and enhanced security. As supply chain attacks have become more prevalent in recent years, SBoM has gained recognition as a critical tool for software security.
Synology recognized the importance of SBoM early on and devoted eight months in 2020 to its implementation. By the integration of SBoM, the PSIRT team is able to assess which versions of our applications may be affected by newly discovered CVE vulnerabilities with speed and agility. The adoption of SBoM not only enables the PSIRT team to conduct a comprehensive examination of the impact but also significantly boosts the efficiency of our incident response process by 50%.
The never-ending pursuit of security
The active collaboration between our security team and product development team enables us to fix security vulnerabilities quickly and efficiently. Our commitment to security also goes beyond just our internal efforts. As a member of the highly respected Forum of Incident Response and Security Teams (FIRST) and the first NAS vendor authorized as a CNA (CVE Numbering Authority) by the world-renowned MITRE Corporation, we are at the forefront of the international cybersecurity community. By partnering with other leading organizations and staying up-to-date on the latest security advancements, we are able to respond to security incidents with unparalleled effectiveness.
From design to release, coding to testing, Synology is fully committed to integrating security into every step of our product development process to safeguard your data.
Last but not least, as a data owner, it is equally as important to take an active role in ensuring the safety of your valuable data. Conducting regular security assessments and building a comprehensive backup strategy are common practices that can help protect your data. Security is a shared responsibility between the vendors and the users. By working together with a trusted vendor, you can minimize the risk of security breaches and ensure the safety of your data.

