When it comes to keeping your personal information secure, don’t take anyone at their word — use encryption.
Since the first Data Privacy Day back in 2007, online privacy threats have multiplied. On top of more traditional threats like phishing — which has been around since at least the early 1990s — users today face more sophisticated risks, including those linked to the widespread adoption of the Internet of Things (IoT).
However, “older” threats remain highly relevant, as evidenced by a recent wave of ransomware attacks that not only lock user data but now have evolved to also threaten to leak it online:
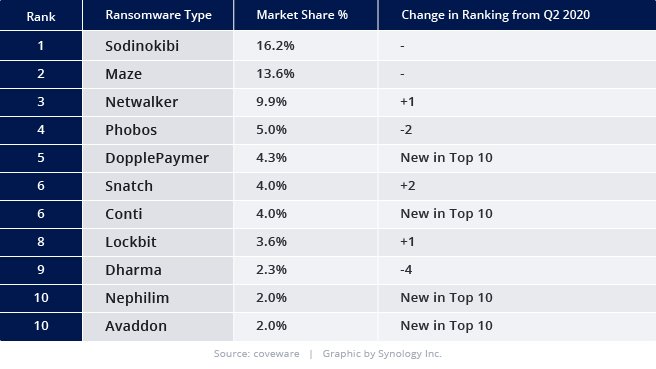
Market share of the most common ransomware attacks as of November 2020 (Coveware)
In 2020, protecting sensitive information online became an even bigger priority. With people sheltering at home to curb the spread of COVID-19, time spent online skyrocketed. The distributed nature of working remotely makes security and backups harder, increasing the likeliness of exposure to cyberattacks, and making remediation harder.
In an early announcement released in March 2020, the FBI warned that increased remote work would let “[c]yber actors exploit vulnerabilities in computer systems and virtual environments to steal sensitive information, target individuals and businesses performing financial transactions, and engage in extortion.”
These concerns are confirmed by a McAfee analysis of last year’s cybercrime data, which estimated cybercrime-related monetary losses at approximately US$945 billion, an 80% increase from 2018.
Staying safe in the cloud era
Data migration to the public cloud appears an unstoppable trend. In addition to on-demand scalability and low up-front costs, public cloud storage and applications offer users high availability, easy sharing, and guaranteed access outside their networks.
Cloud services can be a smart investment for businesses experiencing swings and changes in service demand, and this is reflected in IT decision-makers’ expectations for the coming 18 months:
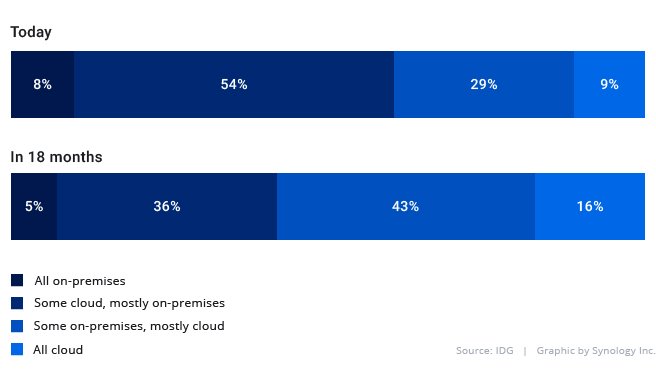
Percentage of IT environment in the public cloud (IDG)
Of course, there are known dangers to using the cloud to store your information. Most commonly known are perhaps the risks of data leaks and of cloud companies’ constantly shifting privacy policies and practices.
In an experiment, a team at Comparitech observed as a database stored insecurely on the cloud was targeted by bad actors an average of 18 times per day. Over the past year, personal information stored by businesses including Pfizer, Razer, nTreatment, and Maropost was exposed as a result of cloud-related mismanagement.
WhatsApp drew the ire of many users this year when a privacy policy update increased integration with Facebook and raised the prospect of having “other, unencrypted data points” shared between the privacy-conscious messaging service and the social network.
An intriguing New York Times’ opinion piece graphically shows how Google’s privacy policy changed — or better, expanded — between 1999 and 2019. It is now at its 24th version:

How the “Information we collect” section in Google’s privacy policy appeared in 2012 (right) vs. 2011 (left) (The New York Times)
A challenge for the best of us
Users are aware of the dangers of the cloud, but time pressure when implementing cloud solutions — a sudden need to back up data, a subscription expiring — and constant changes to already subscribed cloud products mean that managing the privacy of your data is easier said than done.
It is becoming increasingly difficult to know where your data is actually located, and who and when has access to your files. Even when you’ve spent much time studying access permissions, you find yourselves insecure about who and what can read your data. Non-transparent syncing and backups lead to data being stored in several locations, making auditing even more difficult.
Often, working or storing in the cloud offers an effective solution to challenges including remote accessibility, infrastructure complexity, and scalability. For those of us who rely on Software as a Service (SaaS) applications in the cloud for many tasks, it may be impossible to take data protection into our own hands. However, the same doesn’t go for cloud-hosted data storage, backup, and file transfer.
At least for your own data, is there a way that you can be absolutely sure about who has access to specific files or information? A platform-independent method that ensures data are equally protected independent of the device or cloud solution they are stored to?
What you can do, a.k.a. Synology’s Guide to Data Encryption
You may have been told this before: Data encryption, when done well, is the closest to a guarantee that only authorized eyes can take a look at any data you wish to protect.
Encrypted files are unintelligible to anyone — human or machine — as long as they do not have the encryption key that was used to encode the original data. Theoretically, encryption offers the same protection whether your data are on your PC, on your NAS, or in the cloud.
But how do you make sure that the right data is encrypted, and stays so when exported, backed up, or synced? Luckily, if you have a Synology NAS, you already own a great platform to design and manage your personal (or your company’s) encryption strategy.
Using DiskStation Manager (DSM) to start with encryption allows you to keep a good overview of your data encryption and exports. The large number of packages that allow you to apply and manage encryption also means it is incredibly easy to start protecting your data today!
NAS as an encryption platform
We’ve compiled an updated overview of the tools you can leverage to encrypt different types of data — and make sure they stay that way.
Centrally store and encrypt sensitive data
All data stored on Synology NAS are kept in shared folders, the basic directories in DSM. When you set up a shared folder, you can choose to encrypt that folder at creation.
Encrypted shared folders are not automatically mounted on startup (unless configured) and can never be mounted without an encryption key. Encryption keys are also (and should be) separate from administrative credentials. This means they can never be read in case of digital or even physical theft, and are another layer of protection even when administrative accounts are compromised.
Encryption keys can be exported, stored on external devices, or stored locally and encrypted in turn using a password or passphrase. This tutorial takes you through the steps and requirements.
Keep data encrypted when syncing to another NAS
Once files are safely stored in an encrypted folder on your Synology NAS, they need not be decrypted to be transferred to a local or remote secondary NAS.
Just like any other shared folder, encrypted shared folders can be automatically synchronized to any other NAS using Shared Folder Sync. This process creates an identical folder in another location that can only be mounted and read with the original encryption key.
Shared Folder Sync only performs one-way synchronization to your secondary device, making sure that changes or deletions on the secondary server do not affect the original data.
Alternatively, you can use Snapshot Replication to periodically save copies of encrypted folders. This offers the advantage of creating multiple versions of each folder, further protecting against unauthorized changes and allowing you to investigate data incidents by studying file histories.
Both transfer methods apply an additional layer of encryption during the network transfer of your files.
Back up PCs and servers to encrypted storage
The newest iteration of our popular PC and server backup suite Active Backup for Business, currently in Beta, allows you to back up all your Windows and Linux devices to encrypted backup folders on your Synology NAS.
In combination with encryption during transfer — already standard in the current release of the software — this solution helps you make sure that the protection you set up for your computers is never compromised by your backups.
Securely back up your NAS to any location …
When it comes time to securely back up your Synology NAS, Hyper Backup has you covered with a range of backup destinations that includes other NAS, Linux servers, USB devices, and public cloud services including Google, Microsoft, and Backblaze.
This can be done safely because anything you wish to copy, whether files or apps, can be securely encrypted before it even leaves your NAS.
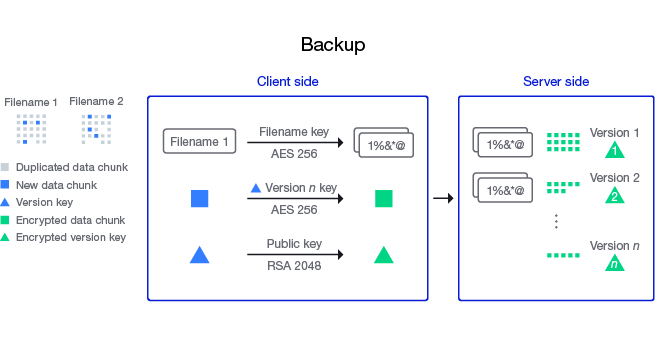
Encryption and versioning with Hyper Backup when storing to C2 Storage explained in our 2019 blog post on the topic (Synology)
The copies Hyper Backup makes can be accessed from the Synology NAS on which they originated or from Windows, macOS, and Linux using the Hyper Backup Explorer tool. In both cases, the original encryption key or a passphrase is necessary to decrypt both files and file names.
… including Synology’s public cloud …
Synology C2 Storage is exclusively designed as a secure cloud location for all your data from Hyper Backup. Data transferred to C2 Storage are encrypted during transfer over the internet, and during long-term storage, when encryption-at-rest protects customer data even in the unlikely event that our data centers are compromised.
While we’ve designed our service with security in mind (as detailed in this white paper), we highly recommend that you enable client-side encryption for all your backups to C2 Storage. That way, your data are unreadable and inaccessible without your private key — even in a worst-case scenario in which your login details or NAS are compromised.
… and keep files encrypted when syncing to Google, Microsoft, Dropbox, or Backblaze
You may wish to keep your files on public cloud services, especially as a way to synchronize files with different teams. But is there a better way to control who has access to your information? And how do you keep your protection centrally managed? Cloud Sync lets you synchronize, protect, and manage files stored on public cloud services centrally from DSM on your NAS.
Cloud Sync lets you set up both one-way and two-way synchronization with solid AES-256 encryption. What makes Cloud Sync particularly versatile is the ability to configure different settings for different folders and customize your protection in detail. We described the app’s design and security features in another white paper.
How about other devices and vendors?
If you are considering encrypting your DSM-managed data, but have not yet set up protection for your PCs or other devices, you may also want to look into encrypting much or all of your Windows, macOS, or Linux installation. Below are links to get you started on other operating systems:
Over to you
Coming right at the beginning of the year, Data Privacy Day reminds us to include a more mindful approach to online privacy in our list of new year’s resolutions.
Start small by carefully reading the privacy policies of cloud services you extend or sign up for this year. However, whether or not you are reassured, consider ways to make encryption part of your digital lifestyle or IT planning.
Research the ways you can enable encryption and other data protection methods on your devices. If you find these hard to implement, at least make sure that everything that leaves your NAS is encrypted.
Consider this: Getting this far into the blog post already got you off to a good start. You made your first investment into better data protection in 2021. But don’t lose momentum, and remember to check the status of your data regularly throughout the year.
If you need help on the way, don’t forget that our Community is there for you. The solution to your problem may be just a few clicks away!
