On April 16, 2021, QNAP released an updated version of the Hybrid Backup Sync (HBS) app (16.0.0415) to add new features and to address a few security issues described in the QNAP Security Advisory QSA-21-13. On April 21, we began to receive user reports about possible ransomware attacks. Unfortunately, it is confirmed later, that the so-called Qlocker ransomware took advantage of one of the patched vulnerabilities in HBS to launch a hostile campaign, targeting QNAP NAS directly connected to the Internet with unpatched old versions of HBS.
The risk of connecting QNAP NAS directly to the Internet without any protection
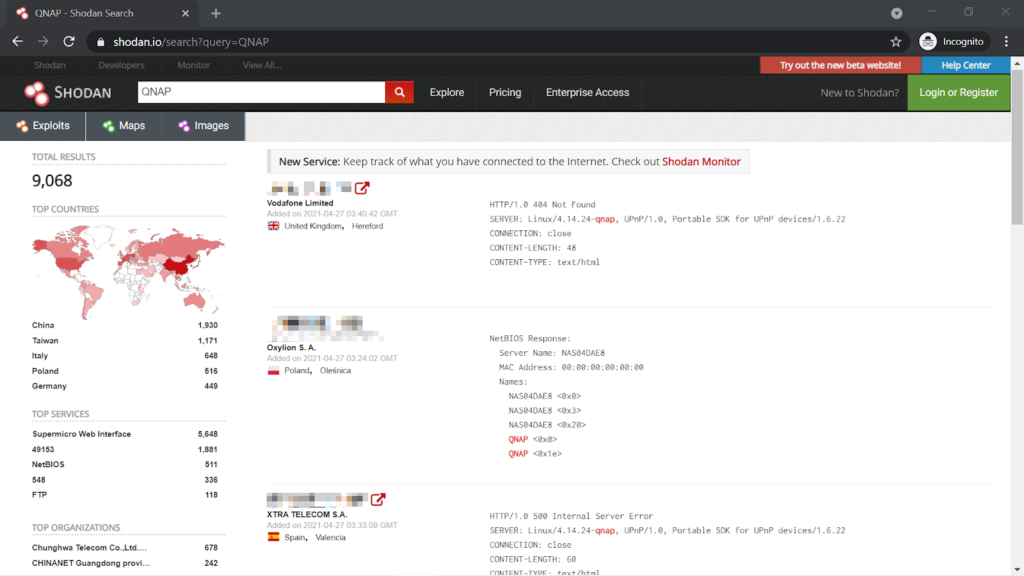
Connecting your QNAP NAS directly to the Internet makes it reachable by anyone in the world. By utilizing specific websites, such as Shodan, and botnets, an attacker could easily discover your device and launch an attack at you.
The definition of “connecting directly to the Internet”
If you have enabled manual port forwarding, auto port forwarding (UPnP, Universal Plug and Play) and demilitarized zone (DMZ) for QNAP NAS in your router or modem configuration, your QNAP NAS is directly connected to the Internet. Some other connection methods that put your QNAP NAS directly on the Internet include obtaining a public IP address (static/PPPoE/DHCP) by QNAP NAS itself.
Our recommended connection methods
If your QNAP NAS is not under the influence of Qlocker, we strongly recommend that you check how your QNAP NAS is connected to the Internet, and make changes if any of the above mentioned methods are used. Doing so will significantly decrease the chance of your QNAP NAS being contacted by unauthorized persons or attackers from the Internet.
It’s preferred that your QNAP NAS stay behind your router and firewall, without a public IP address. You should disable manual port forwarding, auto port forwarding (UPnP, Universal Plug and Play) and demilitarized zone (DMZ) for QNAP NAS in your router configuration.
Instead, enable the VPN server function for your router. When you need access to QNAP NAS from the Internet, first connect to the VPN server on your router, and then connect to your QNAP NAS.
You can also make use of the myQNAPcloud Link service provided by QNAP to access your QNAP NAS. However the transmission could be slightly slower because the traffic is relayed.
Other alternative connection methods include enabling the VPN server on QNAP NAS (by installing the QVPN Service app) or deploying QuWAN, the SD-WAN solution introduced by QNAP. If you do so, you still need to open a very small number of network ports to the Internet. So, we recommend that you take additional steps listed below to further secure your QNAP NAS.
Actions to take If you NAS must be directly connected to the Internet
If, at the discretion of individual users, QNAP NAS is directly connected to the Internet, we recommend the following steps to strengthen your device and to decrease the chance of being penetrated:
- Put QNAP NAS behind your router and firewall. Do not let QNAP NAS obtain a public IP address. Do not use UPnP and DMZ. It’s advised to turn off UPnP on QNAP NAS as well. Manually set up port forwarding in your router configuration only for the network ports required by specific QNAP NAS services.
- Stop or disable services, such as Telnet, SSH, web server, SQL server, phpMyAdmin and PostgreSQL, when not in use.
- Change default external (Internet side) port numbers, such as 21, 22, 80, 443, 8080 and 8081, to customized (randomized) ones. For example, change 8080 to 9527.
- Use only encrypted HTTPS connections, or other types of secure connections (SSH, etc.).
- Install QuFirewall on your QNAP NAS and limit the allowed IP addresses to a specific region or subnet.
- Set up a new administrator account, and disable the default admin account.
- Use strong passwords for all NAS users, including the new administrator account you’ve just created.
- Configure MFA (2-Step Verification) on QNAP NAS.
- Enable auto OS and app updates. Pick a time that works best for you without interrupting your auto backup/sync schedule or other tasks.
- Enable IP access protection to block IP addresses with too many failed login attempts.
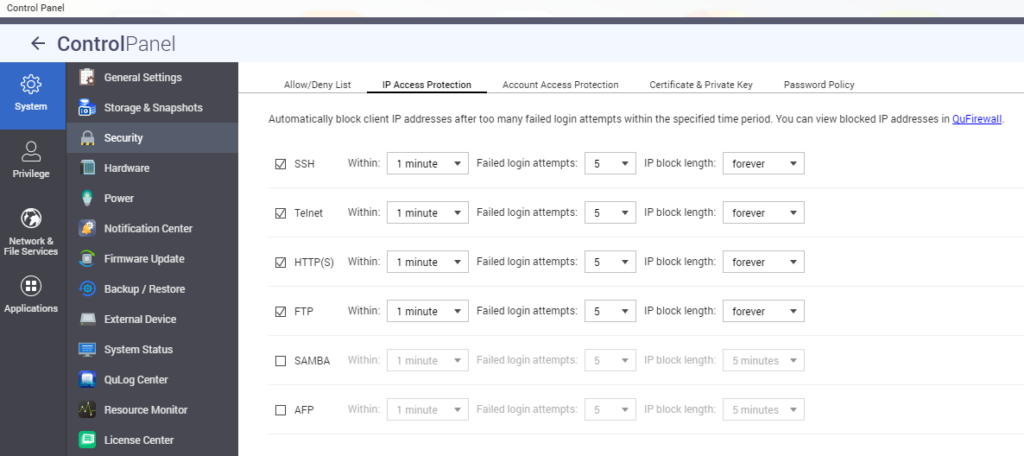
Attackers have been constantly looking for any exploitable weaknesses to take advantage for their own agendas. As a result, QNAP monitors the latest information security intelligence to deliver up-to-date details and software updates, ensuring data security for users. Please work with us and follow the advice and recommendations given in this article, to enhance the resilience of your data/privacy protection strategy.
