Stadiums, universities, and auditoriums are filled with huge crowds of people with various devices—laptops, desktops, tablets, and smartphones—trying to connect to your network. Even when the environment is large and the devices are many, users want a network that allows them to roam freely within the environment without losing speed or dropping connection.
What’s the Problem?
Hundreds, even thousands, of devices trying to access a network at the same time can clog servers. Imagine the first day of classes at a large university, where students and faculty are trying to connect to the campus network. The network DHCP (dynamic host configuration protocol) server must continually assign each new device an IP address, even as the already-connected devices pass traffic. If 6,000 people are trying to connect to the network at the same time, network speed will slow to a crawl.
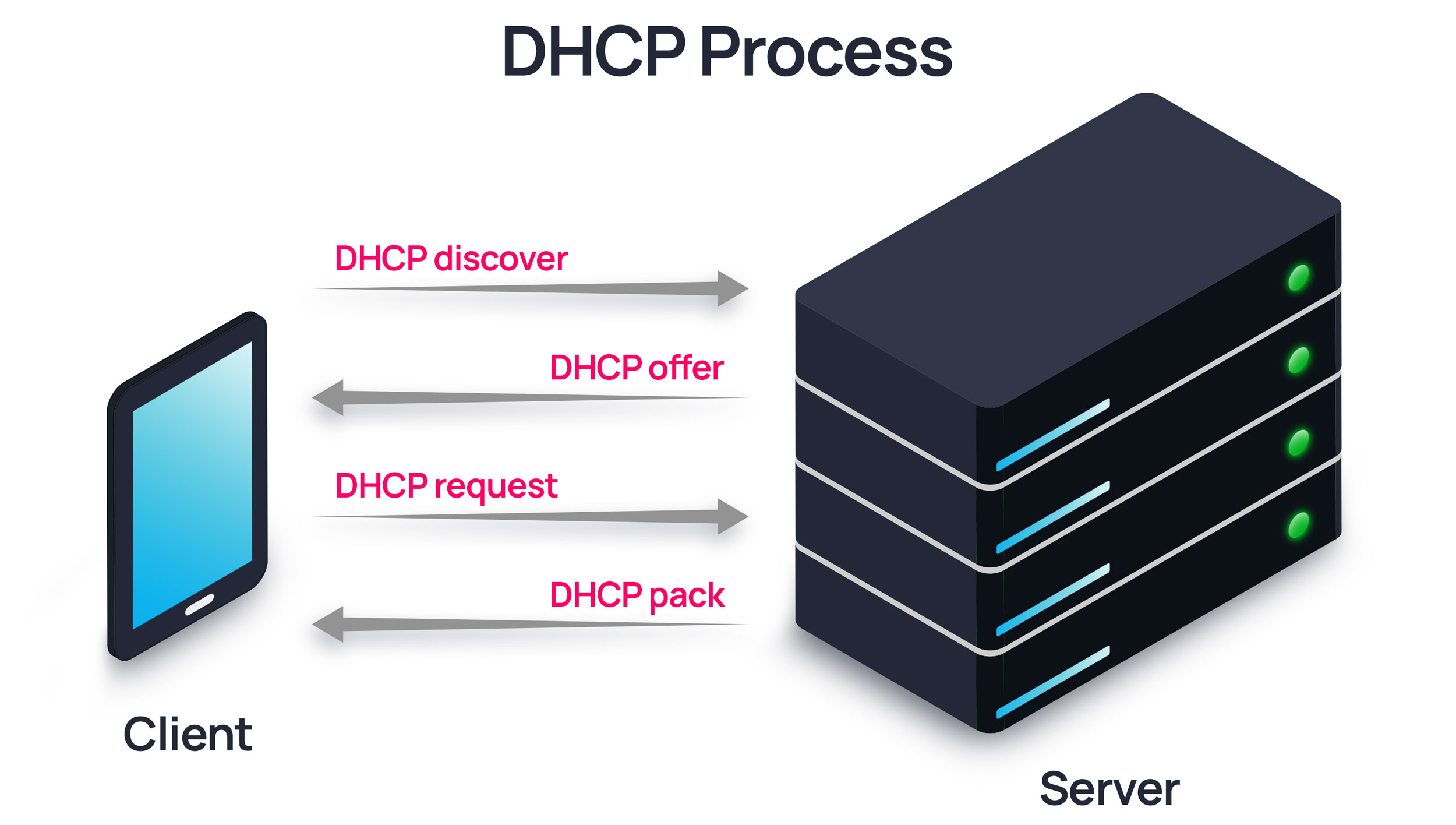
As can be seen in the illustration above, there are four initial steps to connect to a network: The client device automatically lets the server know it wants to connect (DHCP discover), the server offers the device an IP address (DHCP offer), the client device accepts (DHCP request), and the server configures the device and grants access to the network (DHCP pack).
With 6,000 users pinging a server at least four times for a grand total of 24,000 data packs zipping back and forth, you can see how network traffic can stagnate.
What’s the Solution?
VLAN pooling, which is set up by the network engineer, breaks a single network into separate virtual networks (VLANs) to reduce traffic. We could take our imaginary campus network and split it, for example, into four virtual networks with 1,500 users each. There are two key benefits: Not only can each user access and navigate the network faster, but they can also wander between buildings and still maintain a connection with their original VLAN and IP address. Namely, since users are kept on the same VLAN with the same IP address, roaming and the user experience are greatly improved. Likewise, subnets—slightly different from VLANs—use “Layer-3” technology when clients roam between subnets so that devices don’t lose IP address and session connections.
Let’s break this into a smaller example. As you can see in the diagram below, the router at the top is connected to two switches that are connected to access points (APs) in two different campus buildings. The access points will assign a VLAN to a device from a pool of configured VLANs.
Suppose a student’s laptop connects wirelessly to an access point broadcasting the “Students” network which is on VLAN 35 in Building 1 and is assigned an IP address. In that case, they can carry the laptop to Building 2 roaming to the secondary access point without losing connection and still assigned to the same VLAN 35 thus keeping the same IP address.
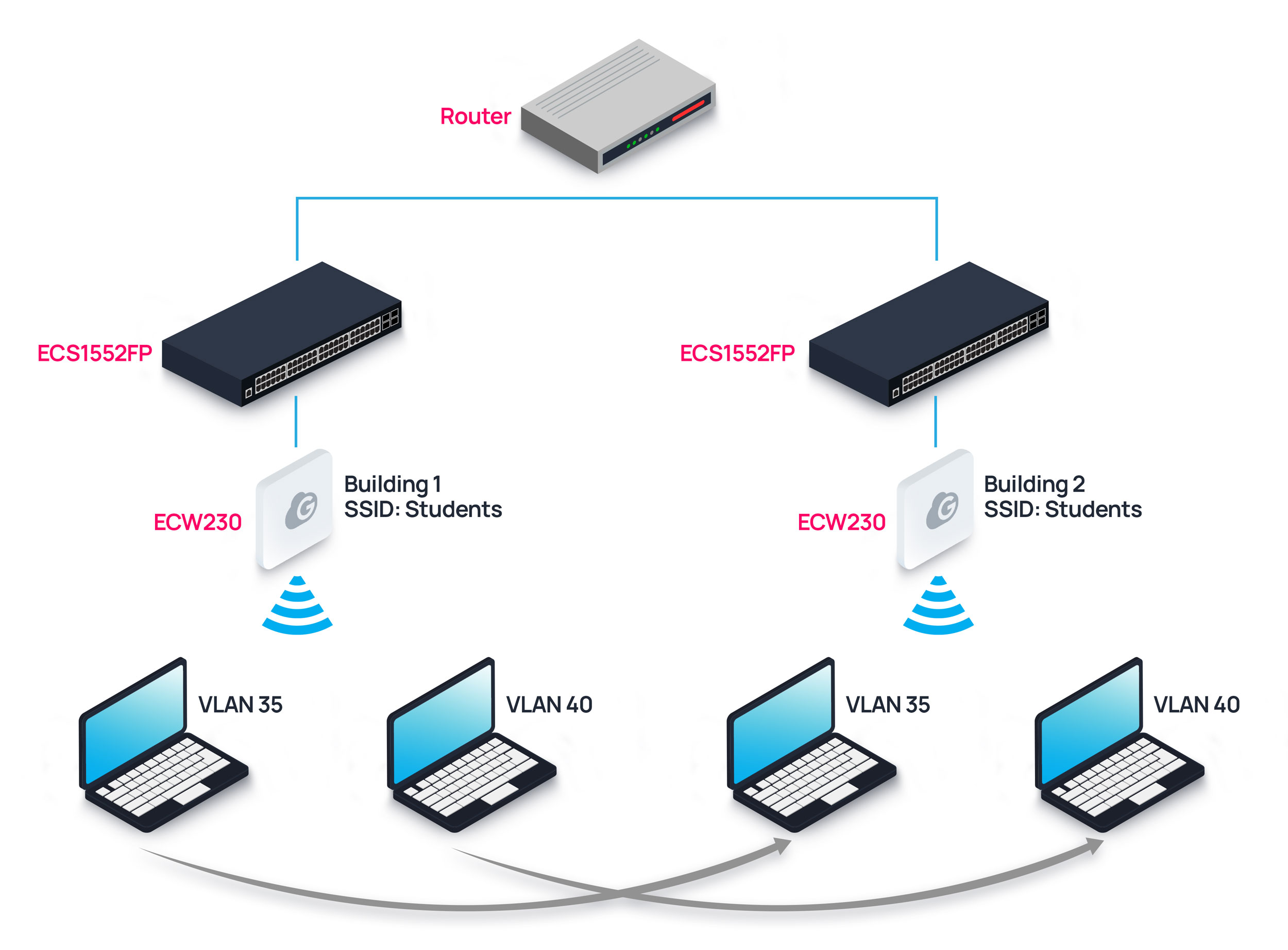
Based on a device MAC address and the number of VLANs in a pool, a “hash” algorithm will generate a super long string of letters and numbers assigning that device to a specific VLAN. No matter where that client goes, the VLAN will follow.
FUN FACT: A hash algorithm is like a blender that turns separate ingredients (MAC address, number of VLANs, etc.) into a frothy milkshake (hash code) that bears no resemblance to the original ingredients and can’t be undone! Hence, it’s very secure.
Under normal circumstances, ALL students would be assigned to the same student SSID and the same single VLAN across the whole campus network so that students would have access to their own resources separate from the faculty SSID. However, VLAN pooling offers a single exclusive SSID for students and assigns their devices to different VLANs resulting in lower network traffic.
Network Devices Understand What’s Going On
Each user device is assigned randomly to a VLAN from a pool of VLANs on the same wired network. Wired networks, switches, and routers recognize VLAN tags and will restrict DHCP broadcasts only to the VLAN to which the client device is assigned. Likewise, each network access point will remember which VLAN each user belongs to and maintain the connection.
Broadcast/Multicast (BCMC) Optimization
While VLAN pooling makes more efficient use of network bandwidth and decreases the chance of network overload, it isn’t guaranteed to prevent it. To make sure your network isn’t flooded with DHCP and similar requests, you can activate an advanced network management feature called broadcast/multicast (BCMC) optimization.
Are you interested in learning more about EnGenius Cloud?
Broadcast flooding, or broadcast “storms,” as they are called, occur when broadcast or multicast packets flood the network, slowing it down and degrading performance. BCMC optimization allows you to restrict unnecessary data packets from flooding your wired and wireless networks, cleaning up the clutter, and smoothing network traffic.
Specifically, BCMC optimization measures broadcast activity in one-second intervals and compares those measurements against a pre-configured threshold. If the threshold is reached, additional broadcast activity is suppressed until the interval is over.
The diagram below illustrates the VLAN pooling and BCMC optimization (suppression) features in the EnGenius Cloud interface.
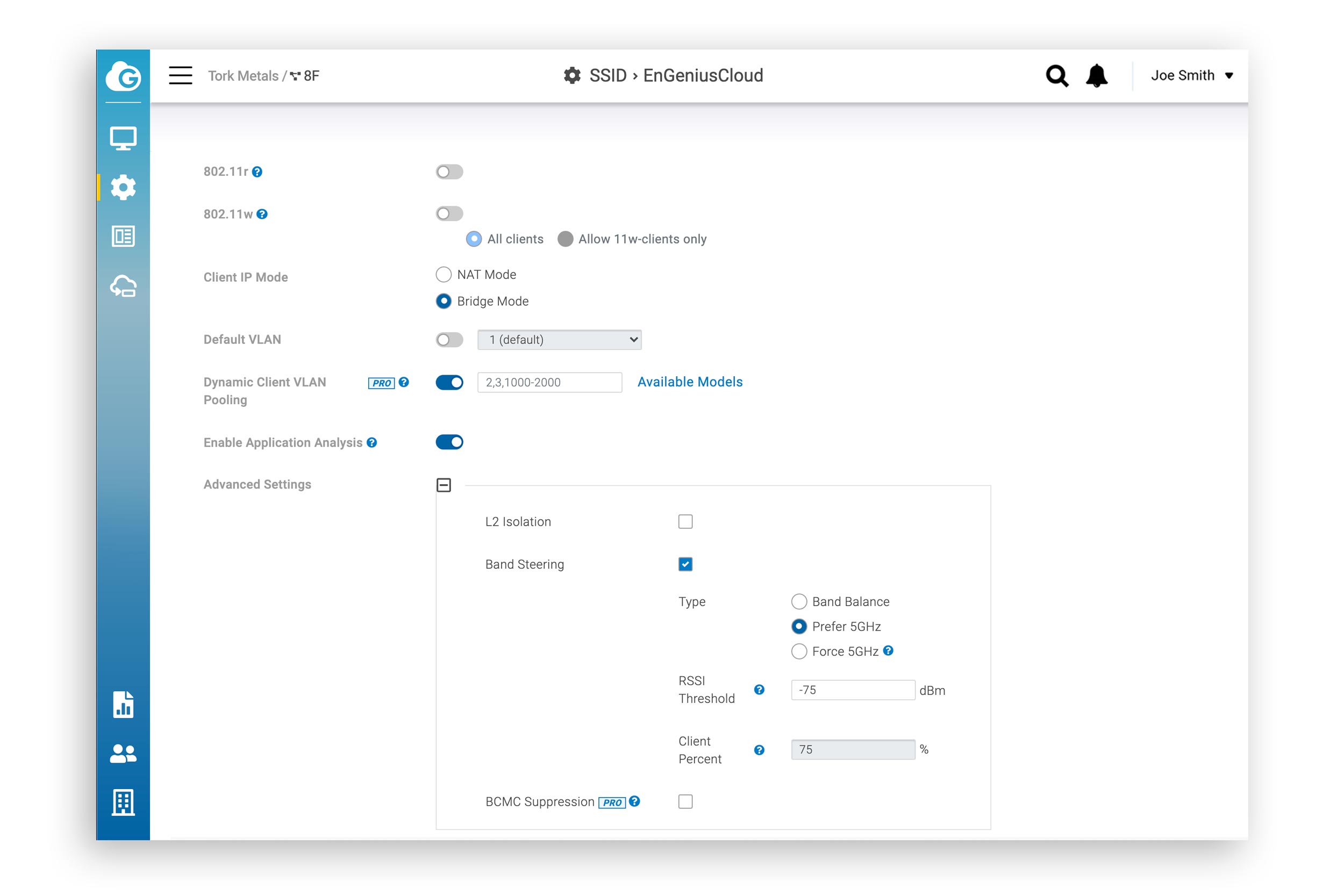
Conclusion
To sum up, dynamic client VLAN pooling means every time the client device connects to the network, it is assigned to the same VLAN and retains the same IP address as it roams to other access points. It reduces network traffic by eliminating the need for the device to connect to the network repeatedly.
Similarly, BCMC optimization (suppression) suppresses wired and wireless broadcasts on client VLANs as needed when traffic extends beyond the configured threshold. Both technologies can work together to significantly mitigate the heavy traffic that often plagues massive networks with numerous users.
