Hundreds of thousands of users fall victim to cyberattacks and the situation is only going to get more complex, especially with the seemingly unstoppable rise of smart devices in our homes.
With this in mind, we have put significant care into equipping Synology Router Manager (SRM) — the operating system that powers every Synology Router — with advanced network functionality that makes it simple to secure any type of network.
In this article, we will explain how to protect your home network and the importance of network segmentation.
The unseen risks
Smart devices bring unprecedented convenience to households but may also pose security risks. IoT devices are vulnerable to ever-increasing threats that vendors may not have prepared for. In fact, some IoT devices completely lack update mechanisms. Furthermore, support is inevitably dropped when a smart device reaches end-of-life status, leaving it vulnerable to attacks.
A compromised IoT device can be silently hijacked to become a part of a botnet or used to monitor your living habits. It may even compromise devices such as computers, notebooks, tablets, and NAS that are connected to your home network. This is called a lateral movement attack, and it commonly originates from a vulnerable NAS or PC infecting IoT devices through an insecure network.
Introducing network segmentation
It should be clear by now that a proactive approach to network security is imperative. We recommend taking the preventative measure of separating your internet-connected devices into different networks. For the average home user, this would be a home (primary) network and an IoT network. For certain individuals, guest networks may be suitable.
The process of creating separate VLANs or virtual local area networks is very simple with Synology Routers. Let’s examine these networks and see how SRM makes it easy to set them up.
Learn more about network segmentation
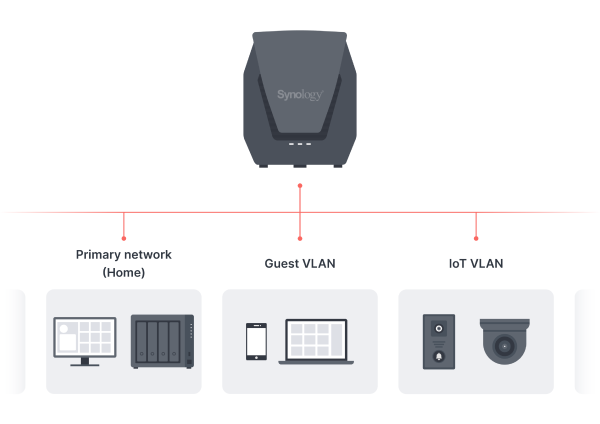
Figure 1. Simply creating these VLANs can significantly increase the security of your network.
Home network
The primary network that is established by default is where most of your devices reside: laptops, tablets, smartphones, smart TVs, smart home hubs, and smart speakers. Although smart TVs, smart speakers, and smart home hubs are IoT devices, they tend to receive consistent security updates and can be left on the primary network. Alternatively, they can be moved to the IoT network and made reachable from specific devices on the main network.
Figure 2. Some of the devices that are typically found in home networks.
Safe Access, SRM’s package for web filtering, integrates Google Safe Browsing and other external databases to identify and block domains that contain unwanted content such as malware, social engineering, potentially harmful applications, and phishing.
Safe Access also features robust parental controls at no extra charge with advanced features such as internet use time limits, content filters, internet use monitoring, and the ability to create custom policies for each device.
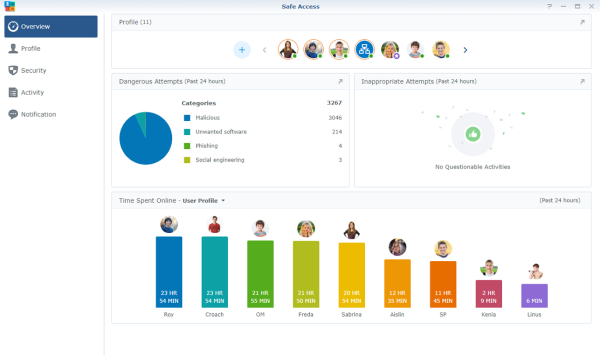
Figure 3. Safe Access’s main dashboard provides a bird’s-eye-view of your network use.
Another security-focused package available in SRM, Threat Prevention, inspects incoming and outgoing packets (internet traffic) and drops them if they are malicious.
Learn more about Threat Prevention
IoT network
IoT devices have taken the market by storm. Everything from refrigerators and coffee machines to dehumidifiers and garage door openers now exists as IoT devices. While they undoubtedly bring conveniences, they can each represent a potential security risk.
Figure 4. Some of the smart devices that are commonly found in households nowadays.
With SRM, you can either isolate them onto their own network or allow one-way communication to devices on other networks via firewall rules. For example, firewall rules can be set to only allow connections initiated from a NAS to communicate with IP cameras, but not the other way around, preventing the risky IoT device from potentially infecting the NAS.
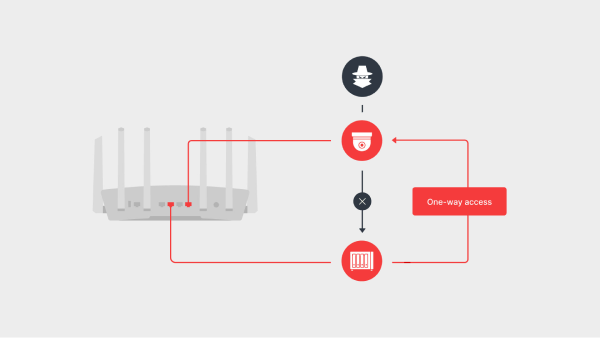
Figure 5. Setting one-way firewall rules to allow for access to the IP cameras from the NAS.
The technology behind Threat Prevention, called Intrusion Prevention System (IPS), is an integral part of many enterprises’ security defenses. This technology is available on all Synology Routers and can be used to protect your home and IoT networks, alerting you if any of your devices have been compromised so you can take action.
To establish an IoT network using VLAN functionality, see our VLAN deployment quick start guide.
Guest network
While guest networks may seem overly cautious, guests’ smartphones may have been incidentally infected with malware without them knowing, and that malware may end up infecting devices on your home network. To avoid the stigma of having a guest network, we recommend giving it a less conspicuous SSID name (do not use the word “guest”).
Creating a guest network with Synology Routers is only a few clicks away. Advanced features, including password rotation, which automatically generates new guest network passwords at regular intervals, and guest network portal, which shows a customizable landing web page to users before they can access the guest network, are available for power users.
Read more about traffic management
Synology Routers have you covered
Our routers give you all the tools you need to ensure safer and more secure internet, with built-in software that works behind the scenes to keep threats at bay while network segmentation functionality makes creating separate networks for different devices simple.
See why they are so highly praised and learn more about all their features here.